PDF Security in C#: Encryption, Permissions, and Protection
IronPDF delivers enterprise-grade security features that go far beyond basic PDF generation, offering robust tools to encrypt, protect, and control access to your PDF documents. In today's landscape where data breaches and unauthorized access pose significant risks, securing sensitive PDF documents has never been more critical. Whether you're handling financial reports, legal contracts, medical records, or classified government documents, IronPDF provides the security infrastructure you need to protect your most sensitive information.
In this in-depth tutorial, we'll explore how you can leverage IronPDF to implement necessary PDF security measures in your C# applications. We'll examine everything from fundamental password protection to advanced military-grade encryption, granular permission controls, and compliance with government security standards. By the end of this article, you'll have the knowledge to implement production-ready PDF security that meets enterprise and regulatory requirements.
Quickstart: Secure Your PDFs with Password Protection
Get started with PDF security using IronPDF in just a few lines of code. This example demonstrates how to apply both encryption and access controls to protect your sensitive documents. Perfect for developers who need enterprise-grade security without complex configuration.
 Get started making PDFs with NuGet now:
Get started making PDFs with NuGet now:
Install IronPDF with NuGet Package Manager
Copy and run this code snippet.
using IronPdf; var pdf = PdfDocument.FromFile("sensitive-document.pdf"); pdf.SecuritySettings.OwnerPassword = "admin-secure-key"; pdf.SecuritySettings.UserPassword = "user-access-key"; pdf.SecuritySettings.AllowUserPrinting = IronPdf.Security.PdfPrintSecurity.NoPrinting; pdf.SecuritySettings.AllowUserCopyPasteContent = false; pdf.SaveAs("secured-document.pdf");Deploy to test on your live environment
Table of Contents
- PDF Security Layers Explained
- Password Protection Fundamentals
- Granular Permission Control
- Opening and Decrypting Protected PDFs
- Military and Classified Document Security
- Security Anti-Patterns to Avoid
 Install with NuGet
Install with NuGetPDF Security Layers Explained
Understanding the layered approach to PDF security is essential for implementing effective document protection. PDF security operates on multiple levels, each providing different types of protection and serving distinct purposes in your overall security strategy.
Understanding Encryption Standards
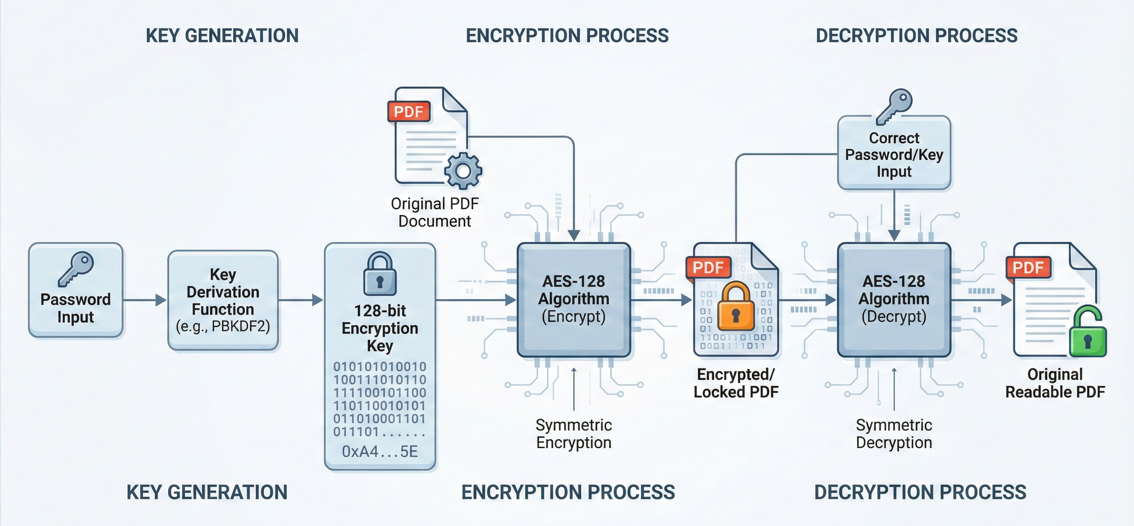
IronPDF secures your sensitive files with enterprise-level 128-bit encryption. Encryption is the backbone of PDF security, converting your document's content into unreadable data that only authorized users can access.
AES-128 Encryption
AES-128 has long been the industry standard for PDF protection. It provides robust security for business documents such as financial files, contracts, and internal records, using a 128-bit key that is computationally infeasible to break via brute force.
The 128-bit encryption standard is compatible with Adobe Acrobat 7 and later versions, ensuring broad compatibility across different PDF readers while maintaining strong security. For most enterprise applications, AES-128 provides an excellent balance between security strength and processing performance.
AES-256 Encryption
With support for 128-bit and 256-bit AES encryption, IronPDF offers flexibility for varying security requirements. AES-256 employs a 256-bit key, making protection exponentially stronger than AES-128. It is used by government agencies for classified documents, meeting requirements for handling sensitive information.
The primary trade-off with AES-256 is slightly increased processing overhead and compatibility considerations—it requires Adobe Acrobat X or later for proper support. However, for applications handling highly sensitive data such as healthcare records subject to HIPAA, financial transactions requiring PCI-DSS compliance, or government documents with classification requirements, the additional security margin is well worth the minimal performance impact.
User vs Owner Passwords
The user password (or open password) is required to open and view the PDF document, while the owner password (or permissions password) controls what actions users can perform on the document. This dual-password system provides flexible security controls for different document workflows.
The user password acts as the primary barrier to document access. When set, anyone attempting to open the PDF must provide this password. This is the password you'd share with authorized readers who should be able to view the document content. Think of it as the "read access" credential.
The owner password serves a different purpose entirely. An owner password is one used to enable and disable all other security settings. This password controls who can modify the document's security settings, change permissions, or remove protection entirely. Even if users can open a document with their user password, they cannot change its security settings or override permission restrictions without the owner's password.
This separation allows for sophisticated access control scenarios. For example, you might distribute a contract with a user password so all parties can read it, but only the document creator (who holds the owner password) can modify security settings or create a version with different restrictions.
:path=/static-assets/pdf/content-code-examples/tutorials/encrypt-pdf-csharp/encrypt-pdf-csharp-pdf-security-user-owner-passwords--1.csusing IronPdf;
var pdf = PdfDocument.FromFile("input.pdf");
// User password required to open/view the PDF
pdf.SecuritySettings.UserPassword = "view-access-2024";
// Owner password required to modify security settings
pdf.SecuritySettings.OwnerPassword = "admin-master-key";
// Disable printing for users without owner password
pdf.SecuritySettings.AllowUserPrinting = IronPdf.Security.PdfPrintSecurity.NoPrint;
// Disable copy/paste of content
pdf.SecuritySettings.AllowUserCopyPasteContent = false;
pdf.SaveAs("output-secured.pdf");
Imports IronPdf
Dim pdf = PdfDocument.FromFile("input.pdf")
' User password required to open/view the PDF
pdf.SecuritySettings.UserPassword = "view-access-2024"
' Owner password required to modify security settings
pdf.SecuritySettings.OwnerPassword = "admin-master-key"
' Disable printing for users without owner password
pdf.SecuritySettings.AllowUserPrinting = IronPdf.Security.PdfPrintSecurity.NoPrint
' Disable copy/paste of content
pdf.SecuritySettings.AllowUserCopyPasteContent = False
pdf.SaveAs("output-secured.pdf")Permission Restriction Framework
Beyond password protection, PDF security includes a comprehensive permissions system that defines exactly what users can do with the document once opened. Permission flags determine whether printing, copying content, editing, annotations, and form data entry are allowed.
The permissions framework operates independently of user passwords. You can set a user password and then specify which operations that user can perform. Alternatively, you can leave the document open without a user password but still restrict certain operations—though this configuration offers limited security since the restrictions can be more easily circumvented without password protection.
Permission controls include:
- Printing restrictions: Control whether users can print at all, and if so, at what quality
- Content extraction: Prevent copying text and images from the document
- Document modification: Restrict editing of the actual document content
- Annotation and commenting: Control whether users can add notes or comments
- Form field manipulation: Determine if users can fill in form fields
- Document assembly: Control page operations like insertion, deletion, or rotation
These granular controls allow you to tailor document security to your specific use case, ensuring users have exactly the access they need—no more, no less.
Password Protection Fundamentals
Implementing password protection in your C# applications using IronPDF is straightforward, but understanding the nuances ensures you apply security correctly and effectively.
Installing IronPDF
Before implementing PDF security features, you need to install IronPDF in your .NET project. The library supports .NET Framework, .NET Core, and .NET 5+, making it compatible with virtually any modern .NET application.
You can install IronPDF via NuGet Package Manager Console:
Install-Package IronPdfOr using the .NET CLI:
dotnet add package IronPdfOnce installed, add the necessary using statements to your code:
using IronPdf;
using IronPdf.Security;using IronPdf;
using IronPdf.Security;Imports IronPdf
Imports IronPdf.SecuritySetting User Password (Required to Open)
You can set the UserPassword property to require a password for opening the file. This represents the most basic level of PDF security—ensuring that only those with the password can view the document content.
:path=/static-assets/pdf/content-code-examples/tutorials/encrypt-pdf-csharp/encrypt-pdf-csharp-pdf-security-set-user-password--2.csusing IronPdf;
var pdf = PdfDocument.FromFile("input.pdf");
// Set user password - anyone opening this PDF must provide this password
pdf.SecuritySettings.UserPassword = "Secure#Password2024!";
pdf.SaveAs("output-protected.pdf");
Imports IronPdf
Dim pdf = PdfDocument.FromFile("input.pdf")
' Set user password - anyone opening this PDF must provide this password
pdf.SecuritySettings.UserPassword = "Secure#Password2024!"
pdf.SaveAs("output-protected.pdf")When a user password is set, IronPDF supports 128-bit encryption to protect the document content. The PDF reader will prompt for this password when anyone attempts to open the file, and without the correct password, the document remains encrypted and unreadable.
Best practices for user passwords:
- Use strong passwords with a mix of uppercase, lowercase, numbers, and special characters
- Avoid common words or easily guessable patterns
- Consider using password generation utilities for maximum security
- Store passwords securely using established password management systems
- Never embed passwords in source code or configuration files in production
Sample Output (Opening a Password Protected PDF)
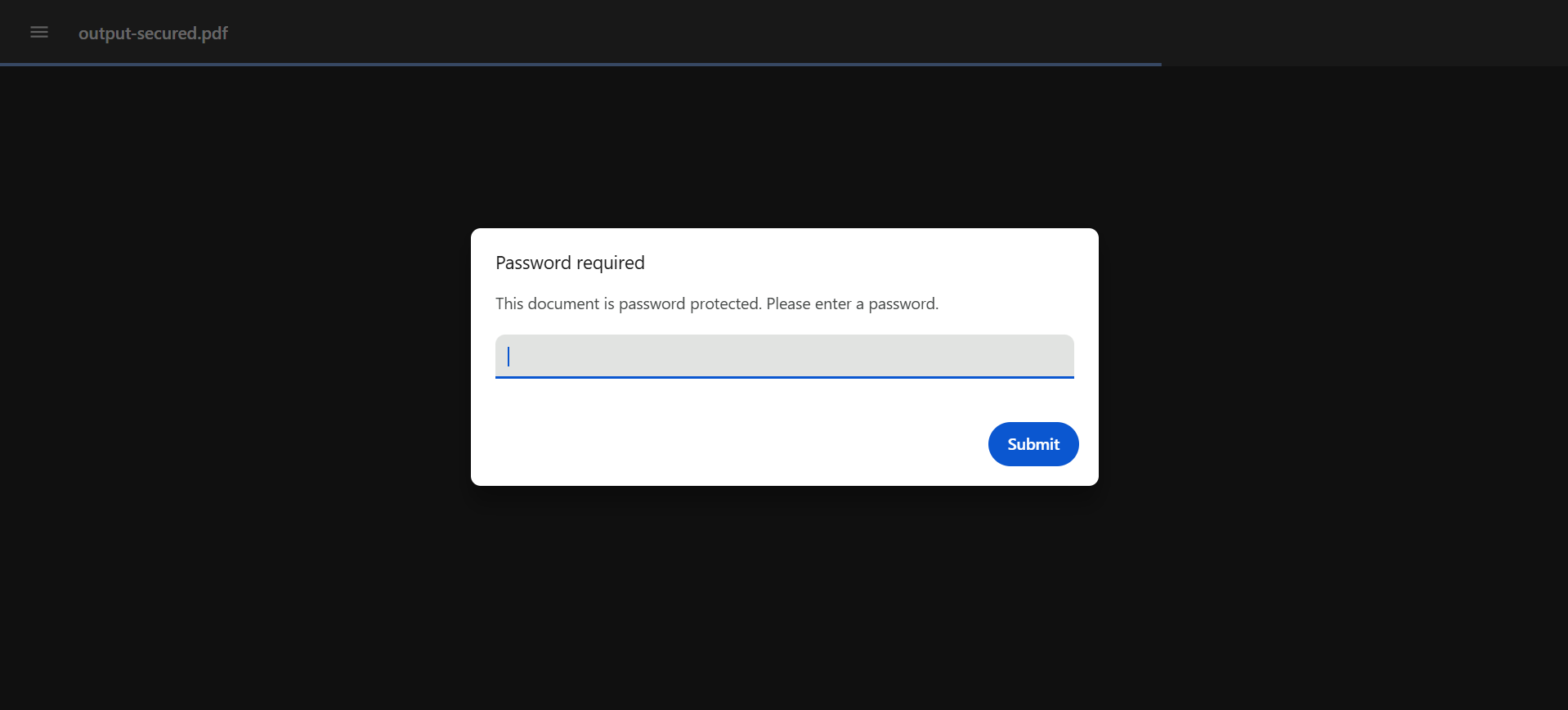
Setting Owner Password (Required to Edit)
The owner password provides a higher level of control over the document. OwnerPassword must be set to a non empty string value for AllowUserCopyPasteContent, AllowUserAnnotations, AllowUserFormData, AllowUserPrinting and AllowUserEdits to be restricted.
:path=/static-assets/pdf/content-code-examples/tutorials/encrypt-pdf-csharp/encrypt-pdf-csharp-pdf-security-set-owner-password--3.csusing IronPdf;
using IronPdf.Security;
var pdf = PdfDocument.FromFile("sample-pdf.pdf");
// Owner password enables restrictions without requiring password to open
pdf.SecuritySettings.OwnerPassword = "admin-control-2024";
// Prevent printing without owner password
pdf.SecuritySettings.AllowUserPrinting = PdfPrintSecurity.NoPrint;
// Disable copy/paste functionality
pdf.SecuritySettings.AllowUserCopyPasteContent = false;
// Prevent any editing without owner password
pdf.SecuritySettings.AllowUserEdits = PdfEditSecurity.NoEdit;
pdf.SaveAs("output-owner-protected.pdf");
Imports IronPdf
Imports IronPdf.Security
Dim pdf = PdfDocument.FromFile("sample-pdf.pdf")
' Owner password enables restrictions without requiring password to open
pdf.SecuritySettings.OwnerPassword = "admin-control-2024"
' Prevent printing without owner password
pdf.SecuritySettings.AllowUserPrinting = PdfPrintSecurity.NoPrint
' Disable copy/paste functionality
pdf.SecuritySettings.AllowUserCopyPasteContent = False
' Prevent any editing without owner password
pdf.SecuritySettings.AllowUserEdits = PdfEditSecurity.NoEdit
pdf.SaveAs("output-owner-protected.pdf")Sample Output
The snippet above creates a document that can be opened by anyone (no user password), but it will still be subject to permission restrictions. To modify the security settings or remove the restrictions, you must know the owner password. This approach is common for public documents where you want to control how they're used but don't necessarily need to restrict viewing.
Encryption Strength Options
IronPDF supports 128-bit encryption for secure document protection, which applies automatically when you set passwords or permissions on your PDF documents. The encryption is transparent—you don't need to explicitly configure encryption algorithms or modes, as IronPDF handles this automatically when you apply security settings.
The 128-bit encryption used by IronPDF provides strong protection suitable for business, legal, and most government applications. The encryption is applied at the content level, meaning the actual text, images, and document structure are encrypted, not just access-controlled.
Granular Permission Control
One of the most powerful aspects of PDF security is the ability to set granular permissions that control exactly what users can do with your documents. IronPDF provides extensive permission controls that go far beyond simple read/write access.
Managing Print Permissions
IronPDF allows you to control printing permissions, helping you manage who can print your PDF documents. Printing restrictions are particularly important for documents containing confidential information, copyrighted material, or data subject to regulatory restrictions.
If print rights are restricted, then the OwnerPassword must be set for the security measure to take effect. This ensures that permission restrictions cannot be easily removed without proper authorization. The following section demonstrates all available print permission levels.
High-Quality vs Low-Quality Print Settings
IronPDF offers sophisticated print permission controls beyond simple allow/deny. The PdfPrintSecurity enumeration provides three levels of print control:
:path=/static-assets/pdf/content-code-examples/tutorials/encrypt-pdf-csharp/encrypt-pdf-csharp-pdf-security-print-quality--4.csusing IronPdf;
using IronPdf.Security;
// Allow low-resolution printing only (150 DPI)
var pdf1 = PdfDocument.FromFile("input.pdf");
pdf1.SecuritySettings.OwnerPassword = "admin-key-2024";
pdf1.SecuritySettings.AllowUserPrinting = PdfPrintSecurity.PrintLowQuality;
pdf1.SaveAs("output-low-res-print.pdf");
// Disable printing completely
var pdf2 = PdfDocument.FromFile("input.pdf");
pdf2.SecuritySettings.OwnerPassword = "secret-admin-key";
pdf2.SecuritySettings.AllowUserPrinting = PdfPrintSecurity.NoPrint;
pdf2.SaveAs("output-no-print.pdf");
// Allow full high-quality printing
var pdf3 = PdfDocument.FromFile("input.pdf");
pdf3.SecuritySettings.OwnerPassword = "owner-key";
pdf3.SecuritySettings.AllowUserPrinting = PdfPrintSecurity.FullPrintRights;
pdf3.SaveAs("output-full-print.pdf");
Imports IronPdf
Imports IronPdf.Security
' Allow low-resolution printing only (150 DPI)
Dim pdf1 = PdfDocument.FromFile("input.pdf")
pdf1.SecuritySettings.OwnerPassword = "admin-key-2024"
pdf1.SecuritySettings.AllowUserPrinting = PdfPrintSecurity.PrintLowQuality
pdf1.SaveAs("output-low-res-print.pdf")
' Disable printing completely
Dim pdf2 = PdfDocument.FromFile("input.pdf")
pdf2.SecuritySettings.OwnerPassword = "secret-admin-key"
pdf2.SecuritySettings.AllowUserPrinting = PdfPrintSecurity.NoPrint
pdf2.SaveAs("output-no-print.pdf")
' Allow full high-quality printing
Dim pdf3 = PdfDocument.FromFile("input.pdf")
pdf3.SecuritySettings.OwnerPassword = "owner-key"
pdf3.SecuritySettings.AllowUserPrinting = PdfPrintSecurity.FullPrintRights
pdf3.SaveAs("output-full-print.pdf")NoPrinting: Completely disables printing functionality in the PDF reader. This is the most restrictive option and is useful for documents that should never be printed, such as digital-only licenses or highly confidential information that should remain solely in electronic form.
LowResolutionPrinting: Allows printing but restricts the output quality to low resolution (typically 150 DPI). This option is valuable for documents where you want to allow reference copies to be printed but want to prevent high-quality reproduction. Common use cases include copyrighted materials, preview copies, or draft documents.
FullPrintRights: Permits unrestricted, high-resolution printing. This gives users the same print quality as if the document were unprotected.
Controlling Copy/Paste Operations
Preventing content copying (disabling text and image selection) is a crucial security feature for protecting intellectual property, confidential data, and copyrighted material.
:path=/static-assets/pdf/content-code-examples/tutorials/encrypt-pdf-csharp/encrypt-pdf-csharp-pdf-security-copy-paste--5.csusing IronPdf;
var pdf = PdfDocument.FromFile("input.pdf");
// Owner password required for copy/paste restrictions
pdf.SecuritySettings.OwnerPassword = "content-protection-key";
// Prevent users from selecting and copying text or images
pdf.SecuritySettings.AllowUserCopyPasteContent = false;
pdf.SaveAs("output-no-copy.pdf");
Imports IronPdf
Dim pdf = PdfDocument.FromFile("input.pdf")
' Owner password required for copy/paste restrictions
pdf.SecuritySettings.OwnerPassword = "content-protection-key"
' Prevent users from selecting and copying text or images
pdf.SecuritySettings.AllowUserCopyPasteContent = False
pdf.SaveAs("output-no-copy.pdf")When copy/paste is disabled, users cannot select and copy text or images from the PDF. This prevents easy extraction of content for unauthorized use, plagiarism, or data theft. However, it's important to understand that this is a PDF reader enforcement—determined attackers with specialized tools may still be able to extract content, which is why encryption and password protection are important complementary measures.
If AllowUserCopyPasteContent is set to false, the OwnerPassword must also be set for the security measure to take effect, ensuring these restrictions cannot be trivially bypassed.
Restricting Document Editing
Document editing restrictions prevent users from modifying the actual content of your PDFs. Disabling editing capabilities ensures that your document's integrity is maintained and unauthorized changes cannot be made.
:path=/static-assets/pdf/content-code-examples/tutorials/encrypt-pdf-csharp/encrypt-pdf-csharp-pdf-security-editing-restrictions--6.csusing IronPdf;
using IronPdf.Security;
// Prevent any content modifications
var pdf1 = PdfDocument.FromFile("input.pdf");
pdf1.SecuritySettings.OwnerPassword = "contract-admin-2024";
pdf1.SecuritySettings.AllowUserEdits = PdfEditSecurity.NoEdit;
pdf1.SaveAs("output-locked.pdf");
// Allow page organization only (rotate, reorder, delete pages)
var pdf2 = PdfDocument.FromFile("input.pdf");
pdf2.SecuritySettings.OwnerPassword = "form-admin-key";
pdf2.SecuritySettings.AllowUserEdits = PdfEditSecurity.EditPages;
pdf2.SaveAs("output-edit-pages.pdf");
// Allow all editing operations
var pdf3 = PdfDocument.FromFile("input.pdf");
pdf3.SecuritySettings.OwnerPassword = "draft-admin";
pdf3.SecuritySettings.AllowUserEdits = PdfEditSecurity.EditAll;
pdf3.SaveAs("output-editable.pdf");
Imports IronPdf
Imports IronPdf.Security
' Prevent any content modifications
Dim pdf1 = PdfDocument.FromFile("input.pdf")
pdf1.SecuritySettings.OwnerPassword = "contract-admin-2024"
pdf1.SecuritySettings.AllowUserEdits = PdfEditSecurity.NoEdit
pdf1.SaveAs("output-locked.pdf")
' Allow page organization only (rotate, reorder, delete pages)
Dim pdf2 = PdfDocument.FromFile("input.pdf")
pdf2.SecuritySettings.OwnerPassword = "form-admin-key"
pdf2.SecuritySettings.AllowUserEdits = PdfEditSecurity.EditPages
pdf2.SaveAs("output-edit-pages.pdf")
' Allow all editing operations
Dim pdf3 = PdfDocument.FromFile("input.pdf")
pdf3.SecuritySettings.OwnerPassword = "draft-admin"
pdf3.SecuritySettings.AllowUserEdits = PdfEditSecurity.EditAll
pdf3.SaveAs("output-editable.pdf")The PdfEditSecurity enumeration provides granular control over what types of edits are permitted:
NoEdit: Completely prevents any modifications to the document content. This is the most restrictive setting and ensures the document cannot be altered in any way.
AddOrModifyTextAnnotations: Allows users to add text annotations and comments but prevents direct modification of the document content. This is useful for review workflows where you want feedback but want to preserve the original document.
FillInFormsAndSignatures: Permits filling in form fields and adding signatures while preventing other edits. This is the standard setting for PDF forms that need to be filled out but not otherwise modified.
DocumentAssemblyAndTextAnnotations: Allows document assembly operations (like page insertion or deletion) as well as text annotations.
AllEditRights: Permits all editing operations without restriction.
Managing Annotations and Comments
AllowUserAnnotations controls whether or not users can annotate the PDF. Annotation control is particularly important in legal, compliance, and collaborative document workflows.
:path=/static-assets/pdf/content-code-examples/tutorials/encrypt-pdf-csharp/encrypt-pdf-csharp-pdf-security-annotations--7.csusing IronPdf;
var pdf = PdfDocument.FromFile("input.pdf");
// Owner password required for annotation restrictions
pdf.SecuritySettings.OwnerPassword = "legal-admin-2024";
// Prevent adding comments, highlights, or other markup
pdf.SecuritySettings.AllowUserAnnotations = false;
pdf.SaveAs("output-no-annotations.pdf");
Imports IronPdf
Dim pdf = PdfDocument.FromFile("input.pdf")
' Owner password required for annotation restrictions
pdf.SecuritySettings.OwnerPassword = "legal-admin-2024"
' Prevent adding comments, highlights, or other markup
pdf.SecuritySettings.AllowUserAnnotations = False
pdf.SaveAs("output-no-annotations.pdf")Disabling annotations prevents users from adding comments, highlights, markup, or any other annotations to the document. This ensures the document remains pristine and prevents confusion caused by unauthorized annotations or comments.
Common use cases for disabled annotations include:
- Final versions of legal contracts
- Official company documentation
- Regulatory submissions
- Published reports that should not be marked up
- Certified or notarized documents
Conversely, enabling annotations while restricting editing is valuable for review processes where you want feedback but want to maintain the integrity of the underlying document.
For a more detailed explanation of the code snippets above and to explore additional security functionality, please refer to our comprehensive how-to guide.
Opening and Decrypting Protected PDFs
Working with protected PDFs programmatically requires understanding how to properly supply credentials and handle encrypted documents in your code.
Supplying Passwords Programmatically
While loading your PDF file using PdfDocument.FromFile, you can pass the password to open the encrypted PDF as a second parameter. This allows your application to work with protected documents without user intervention.
:path=/static-assets/pdf/content-code-examples/tutorials/encrypt-pdf-csharp/encrypt-pdf-csharp-pdf-security-open-encrypted--8.csusing IronPdf;
// Open password-protected PDF
var password = "user-access-2024";
var pdf = PdfDocument.FromFile("protected.pdf", password);
// Work with the decrypted document
var text = pdf.ExtractAllText();
// Modify and save
pdf.SaveAs("output-processed.pdf");
// Note: For production, use secure password storage (environment variables, key vaults)
Imports IronPdf
' Open password-protected PDF
Dim password As String = "user-access-2024"
Dim pdf As PdfDocument = PdfDocument.FromFile("protected.pdf", password)
' Work with the decrypted document
Dim text As String = pdf.ExtractAllText()
' Modify and save
pdf.SaveAs("output-processed.pdf")
' Note: For production, use secure password storage (environment variables, key vaults)This approach is essential for automated workflows where protected PDFs need to be processed programmatically. Common scenarios include:
- Automated document processing pipelines
- Scheduled report generation
- Batch conversion operations
- Integration with document management systems
- Automated archival processes
Important security considerations:
- Never hardcode passwords in your source code
- Use secure configuration management (Azure Key Vault, AWS Secrets Manager, etc.)
- Implement proper access controls for password storage
- Use environment variables or secure configuration files
- Consider using certificate-based security for highly sensitive applications
Removing Security Restrictions
To remove passwords and encryption, use the RemovePasswordsAndEncryption method. This functionality is crucial when you need to strip security from documents, but it requires proper authorization to prevent unauthorized access.
:path=/static-assets/pdf/content-code-examples/tutorials/encrypt-pdf-csharp/encrypt-pdf-csharp-pdf-security-remove-restrictions--9.csusing IronPdf;
var pdf = PdfDocument.FromFile("protected.pdf", "owner-password-2024");
pdf.SecuritySettings.RemovePasswordsAndEncryption();
pdf.SaveAs("output-unprotected.pdf");
Imports IronPdf
Dim pdf = PdfDocument.FromFile("protected.pdf", "owner-password-2024")
pdf.SecuritySettings.RemovePasswordsAndEncryption()
pdf.SaveAs("output-unprotected.pdf")Removing all user and owner password security for a PDF document also disables content encryption. The resulting document will be completely unprotected and can be opened, viewed, edited, and printed without any restrictions.
When to remove security:
- Preparing documents for archival systems that cannot handle encrypted PDFs
- Migrating to different security mechanisms
- Creating publicly distributable versions of previously protected documents
- Resolving compatibility issues with older PDF readers
- Preparing documents for integration with systems that require unencrypted input
Batch Processing Encrypted Files
When working with multiple protected PDFs, you can implement batch processing to handle entire directories of encrypted documents efficiently.
:path=/static-assets/pdf/content-code-examples/tutorials/encrypt-pdf-csharp/encrypt-pdf-csharp-pdf-security-batch-processing--10.csusing IronPdf;
using System;
using System.IO;
string inputDir = "./input";
string outputDir = "./output";
Directory.CreateDirectory(outputDir);
var pdfFiles = Directory.GetFiles(inputDir, "*.pdf");
string password = "batch-process-2024";
foreach (var pdfPath in pdfFiles)
{
try
{
PdfDocument pdf;
try
{
pdf = PdfDocument.FromFile(pdfPath, password);
}
catch
{
pdf = PdfDocument.FromFile(pdfPath);
}
var text = pdf.ExtractAllText();
pdf.SecuritySettings.RemovePasswordsAndEncryption();
string fileName = Path.GetFileName(pdfPath);
string outputPath = Path.Combine(outputDir, fileName);
pdf.SaveAs(outputPath);
}
catch (Exception ex)
{
// Handle errors as needed
}
}
Imports IronPdf
Imports System
Imports System.IO
Dim inputDir As String = "./input"
Dim outputDir As String = "./output"
Directory.CreateDirectory(outputDir)
Dim pdfFiles = Directory.GetFiles(inputDir, "*.pdf")
Dim password As String = "batch-process-2024"
For Each pdfPath In pdfFiles
Try
Dim pdf As PdfDocument
Try
pdf = PdfDocument.FromFile(pdfPath, password)
Catch
pdf = PdfDocument.FromFile(pdfPath)
End Try
Dim text = pdf.ExtractAllText()
pdf.SecuritySettings.RemovePasswordsAndEncryption()
Dim fileName As String = Path.GetFileName(pdfPath)
Dim outputPath As String = Path.Combine(outputDir, fileName)
pdf.SaveAs(outputPath)
Catch ex As Exception
' Handle errors as needed
End Try
NextThis pattern is valuable for enterprise scenarios where you need to:
- Process entire document repositories
- Apply consistent security policies across document sets
- Migrate encrypted documents to new security standards
- Perform bulk analysis or content extraction from protected documents
- Implement automated compliance workflows
For batch processing, consider implementing:
- Proper error handling for invalid passwords or corrupted files
- Logging of security operations for audit trails
- Progress reporting for long-running operations
- Parallel processing for improved performance on large document sets
- Secure cleanup of temporary decrypted files
Military and Classified Document Security
For organizations handling classified information, government documents, or data requiring military-grade security, PDF protection extends far beyond basic password protection into full-scale security frameworks.
Beyond Password Protection
While password protection and encryption form the foundation of PDF security, truly secure document handling requires a layered approach that addresses multiple attack vectors and compliance requirements.
Multi-factor authentication integration: For classified documents, password protection alone is insufficient. Consider implementing systems where PDF access requires both a password and additional authentication factors, such as smart card credentials, hardware security tokens, or biometric verification.
Hardware security modules (HSM): For HSM based solutions, the private key cannot be exported. Instead, firmware on the USB key does the signing. This ensures that cryptographic keys never leave the secure hardware environment, providing the highest level of key protection for digital signatures on classified documents.
Encryption at rest and in transit: Classified documents require protection not only when stored but also during transmission. Implement transport layer security (TLS) for any network transmission of protected PDFs, and ensure storage systems use full-disk encryption with FIPS 140-2 validated encryption modules.
Document Sanitization for Declassification
Sanitizing a classified document removes enough information to reduce the classification from a higher level to a lower one. This process is critical for government agencies and contractors handling classified material that needs eventual public release.
Important: Always remove sensitive content entirely rather than obscuring it visually—see Visual obscuration in the Security Anti-Patterns section for why this matters.
Proper sanitization requires clearing all metadata fields, custom properties, and hidden content programmatically. PDF documents often retain previous versions, comments, and embedded data that can contain classified information. See the Metadata Leaks section below for implementation details and a complete sanitization checklist.
For declassification workflows, implement a multi-step process:
- Identify classified content requiring redaction
- Remove (not obscure) classified text and images
- Strip all metadata and hidden content
- Remove embedded files and scripts
- Verify sanitization through automated and manual review
- Apply appropriate downgraded classification markings
- Maintain audit trail of declassification actions
Audit Trails and Access Logging
For classified documents, comprehensive audit trails are not just best practice—they're often mandatory under regulations like Executive Order 13526 for national security information.
:path=/static-assets/pdf/content-code-examples/tutorials/encrypt-pdf-csharp/encrypt-pdf-csharp-pdf-security-audit-logging--11.csusing IronPdf;
using System;
using System.IO;
using System.Text.Json;
var handler = new SecureDocumentHandler();
handler.OpenClassifiedDocument(
"classified.pdf",
"classified-password",
"john.doe@agency.gov",
"192.168.1.100"
);
handler.LogPrintOperation(
"classified.pdf",
"john.doe@agency.gov",
"192.168.1.100"
);
public class PdfAuditLog
{
public DateTime Timestamp { get; set; }
public string Username { get; set; }
public string Operation { get; set; }
public string DocumentPath { get; set; }
public string IpAddress { get; set; }
public bool Success { get; set; }
public string Details { get; set; }
}
public class SecureDocumentHandler
{
private readonly string auditLogPath = "./logs/audit.log";
public void OpenClassifiedDocument(string documentPath, string password, string username, string ipAddress)
{
var auditEntry = new PdfAuditLog
{
Timestamp = DateTime.UtcNow,
Username = username,
Operation = "OPEN",
DocumentPath = documentPath,
IpAddress = ipAddress,
Success = false,
Details = ""
};
try
{
var pdf = PdfDocument.FromFile(documentPath, password);
auditEntry.Success = true;
auditEntry.Details = "Document opened successfully";
LogAuditEntry(auditEntry);
}
catch (Exception ex)
{
auditEntry.Success = false;
auditEntry.Details = $"Failed: {ex.Message}";
LogAuditEntry(auditEntry);
throw;
}
}
public void LogPrintOperation(string documentPath, string username, string ipAddress)
{
var auditEntry = new PdfAuditLog
{
Timestamp = DateTime.UtcNow,
Username = username,
Operation = "PRINT",
DocumentPath = documentPath,
IpAddress = ipAddress,
Success = true,
Details = "Document printed"
};
LogAuditEntry(auditEntry);
}
private void LogAuditEntry(PdfAuditLog entry)
{
Directory.CreateDirectory(Path.GetDirectoryName(auditLogPath));
string jsonEntry = JsonSerializer.Serialize(entry);
File.AppendAllText(auditLogPath, jsonEntry + Environment.NewLine);
}
}
Imports IronPdf
Imports System
Imports System.IO
Imports System.Text.Json
Dim handler As New SecureDocumentHandler()
handler.OpenClassifiedDocument("classified.pdf", "classified-password", "john.doe@agency.gov", "192.168.1.100")
handler.LogPrintOperation("classified.pdf", "john.doe@agency.gov", "192.168.1.100")
Public Class PdfAuditLog
Public Property Timestamp As DateTime
Public Property Username As String
Public Property Operation As String
Public Property DocumentPath As String
Public Property IpAddress As String
Public Property Success As Boolean
Public Property Details As String
End Class
Public Class SecureDocumentHandler
Private ReadOnly auditLogPath As String = "./logs/audit.log"
Public Sub OpenClassifiedDocument(documentPath As String, password As String, username As String, ipAddress As String)
Dim auditEntry As New PdfAuditLog With {
.Timestamp = DateTime.UtcNow,
.Username = username,
.Operation = "OPEN",
.DocumentPath = documentPath,
.IpAddress = ipAddress,
.Success = False,
.Details = ""
}
Try
Dim pdf = PdfDocument.FromFile(documentPath, password)
auditEntry.Success = True
auditEntry.Details = "Document opened successfully"
LogAuditEntry(auditEntry)
Catch ex As Exception
auditEntry.Success = False
auditEntry.Details = $"Failed: {ex.Message}"
LogAuditEntry(auditEntry)
Throw
End Try
End Sub
Public Sub LogPrintOperation(documentPath As String, username As String, ipAddress As String)
Dim auditEntry As New PdfAuditLog With {
.Timestamp = DateTime.UtcNow,
.Username = username,
.Operation = "PRINT",
.DocumentPath = documentPath,
.IpAddress = ipAddress,
.Success = True,
.Details = "Document printed"
}
LogAuditEntry(auditEntry)
End Sub
Private Sub LogAuditEntry(entry As PdfAuditLog)
Directory.CreateDirectory(Path.GetDirectoryName(auditLogPath))
Dim jsonEntry As String = JsonSerializer.Serialize(entry)
File.AppendAllText(auditLogPath, jsonEntry & Environment.NewLine)
End Sub
End ClassEssential audit elements:
- Access events: Log every document open, view, print, and close operation
- User identification: Record the authenticated identity of everyone accessing the document
- Timestamp: Maintain precise time records with synchronized clocks
- Operation type: Distinguish between viewing, printing, editing, and other operations
- Outcome: Record success or failure of operations
- Source information: Capture IP addresses, machine identifiers, and location data where available
Audit log protection: Audit logs themselves become sensitive and must be protected:
- Store logs separately from the documents they track
- Apply encryption to audit data
- Implement append-only log storage to prevent tampering
- Use cryptographic signatures to ensure log integrity
- Regular backup to secure, off-site locations
- Define retention periods consistent with regulatory requirements
Combining Encryption with Digital Signatures
Digital signatures provide authentication and integrity for PDF documents. By using IronPDF, you can ensure that your document is signed by a verified source and that it hasn't been altered since the signature was applied.
For classified documents, combining encryption with digital signatures provides both confidentiality and authenticity:
:path=/static-assets/pdf/content-code-examples/tutorials/encrypt-pdf-csharp/encrypt-pdf-csharp-pdf-security-digital-signatures--12.csusing IronPdf;
using IronPdf.Signing;
using System.Security.Cryptography.X509Certificates;
var pdf = PdfDocument.FromFile("input.pdf");
// Apply encryption
pdf.SecuritySettings.UserPassword = "view-classified-2024";
pdf.SecuritySettings.OwnerPassword = "admin-classified-2024";
// Digital signature requires external certificate file (certificate.pfx)
// In production: use certificates from trusted Certificate Authorities and secure hardware (HSM)
var certificate = new X509Certificate2("certificate.pfx", "cert-password");
var signature = new PdfSignature(certificate)
{
SignatureContact = "security@agency.gov",
SignatureReason = "Document Certification",
SignatureLocation = "Washington DC, USA"
};
pdf.Sign(signature);
pdf.SaveAs("output-signed-encrypted.pdf");
Imports IronPdf
Imports IronPdf.Signing
Imports System.Security.Cryptography.X509Certificates
Dim pdf = PdfDocument.FromFile("input.pdf")
' Apply encryption
pdf.SecuritySettings.UserPassword = "view-classified-2024"
pdf.SecuritySettings.OwnerPassword = "admin-classified-2024"
' Digital signature requires external certificate file (certificate.pfx)
' In production: use certificates from trusted Certificate Authorities and secure hardware (HSM)
Dim certificate = New X509Certificate2("certificate.pfx", "cert-password")
Dim signature = New PdfSignature(certificate) With {
.SignatureContact = "security@agency.gov",
.SignatureReason = "Document Certification",
.SignatureLocation = "Washington DC, USA"
}
pdf.Sign(signature)
pdf.SaveAs("output-signed-encrypted.pdf")Digital signature components for classified documents:
Certificate chain validation: The permitted uses of a certificate are listed in the ASN.1 encoded extension attributes of the certificate. For classified documents, ensure certificates are issued by approved Certificate Authorities and include proper Extended Key Usage attributes.
Timestamp authority: Any timestamp should also include the Timestamp Service Authority (TSA) certificate. This provides cryptographic proof of when the document was signed, essential for legal and compliance requirements.
Long-term validation (LTV): For documents requiring validation years into the future (common with classified material), implement LTV signatures that include all validation information within the document itself, ensuring signature verification even if certificate authorities are no longer accessible.
Non-repudiation: Digital signatures provide non-repudiation—the signer cannot deny having signed the document. This is crucial for classified documents where accountability and attribution are paramount.
For more detailed guidance on implementing digital signatures with IronPDF, refer to our detailed signing tutorial.
Security Anti-Patterns to Avoid
Understanding what doesn't work in PDF security is as important as knowing what does. These anti-patterns represent common mistakes that create a false sense of security while leaving documents vulnerable.
Easily Bypassed "Security" Methods
Many approaches that appear to provide security are trivially defeated by anyone with basic knowledge or freely available tools.
JavaScript-based protection: It is useless because you have to rely on users having JS enabled in their viewing app. Users can modify JS in the browser, block or stop code execution. Never rely on JavaScript for security enforcement, as it operates entirely within the user's control.
Password obscurity: Using weak passwords, predictable patterns, or relying on obscurity rather than strength provides no real protection. Common mistakes include:
- Using document titles or dates as passwords
- Sequential numbers or repeated characters
- Default passwords like "password" or "12345"
- Sharing passwords through insecure channels
- Storing passwords in the PDF properties or metadata
Visual obscuration: Adding an image layer over sensitive text to obscure it, without removing the underlying text provides no security. The original text remains in the PDF structure and can be extracted with basic PDF tools or even simple copy-paste operations.
Proprietary "encryption": Some systems claim to use proprietary encryption algorithms. This violates Kerckhoffs's principle—security should rely on key secrecy, not algorithm secrecy. Always use well-established, peer-reviewed encryption standards like AES.
JavaScript Vulnerabilities in PDFs
Despite efforts by Adobe to limit the impact of malicious JavaScript, it remains a vector that sophisticated attackers can exploit to compromise data, users, and their devices.
The JavaScript threat landscape:
CVE-2024-4367 allows attackers to execute arbitrary JavaScript code when a malicious PDF file is opened. This vulnerability, which affected PDF.js (used by millions of websites and Firefox), demonstrates how PDF JavaScript can be exploited for remote code execution.
Common JavaScript attack vectors in PDFs:
Code execution: Malicious macros and embedded scripts with weak controls allow embedded code to run on open, installing malware or granting unauthorized access. JavaScript in PDFs can access local file systems, make network connections, and execute arbitrary code in some contexts.
Data exfiltration: Sensitive data could be leaked to hackers without your knowledge, such as form data, login credentials, and local files. JavaScript can read form fields, access document content, and transmit data to remote servers.
Cross-site scripting (XSS): In environments where PDF.js is embedded without adequate security measures, this vulnerability could enable Cross-site Scripting (XSS) attacks, data breaches, unauthorized actions, or even full account takeovers.
Mitigation strategies:
:path=/static-assets/pdf/content-code-examples/tutorials/encrypt-pdf-csharp/encrypt-pdf-csharp-pdf-security-javascript-mitigation--13.csusing IronPdf;
using IronPdf.Rendering;
var pdf = PdfDocument.FromFile("input.pdf");
// Prevent JavaScript injection by disabling editing
pdf.SecuritySettings.OwnerPassword = "admin-secure-2024";
pdf.SecuritySettings.AllowUserEdits = IronPdf.Security.PdfEditSecurity.NoEdit;
pdf.SaveAs("output-hardened.pdf");
Imports IronPdf
Imports IronPdf.Rendering
Dim pdf = PdfDocument.FromFile("input.pdf")
' Prevent JavaScript injection by disabling editing
pdf.SecuritySettings.OwnerPassword = "admin-secure-2024"
pdf.SecuritySettings.AllowUserEdits = IronPdf.Security.PdfEditSecurity.NoEdit
pdf.SaveAs("output-hardened.pdf")Additional protective measures:
- Implement Content Security Policy (CSP) headers when displaying PDFs in web applications
- Disable JavaScript in PDFs. Many exploits take advantage of JavaScript vulnerabilities
- Use PDF readers with sandboxing capabilities to isolate PDF execution
- Keep PDF software updated to patch known vulnerabilities
- Implement network-level filtering to block connections from PDF JavaScript
- Enforce and update network-based URL filters to limit an enterprise asset from connecting to potentially malicious or unapproved websites
Metadata Leaks in "Secured" Documents
PDF metadata isn't visible on the page, but it can still reveal a lot. Author names, software versions, dates, and internal notes all sit behind the scenes and can be pulled out in seconds.
Common metadata security risks:
Personal identifiable information (PII): External viewers can pull author names, internal project codes, or document subjects and learn how your teams work and who is involved. Even documents with strong password protection may leak sensitive metadata if not properly sanitized.
Software version disclosure: Metadata often includes software and version details. Attackers can use this to guess your environment and look for known exploits. This information provides attackers with a roadmap for targeted attacks.
Edit history and version information: Some workflows add edit details into metadata or related fields. In legal, HR, or PR contexts, that extra history can raise questions you didn't expect. Previous versions, comments, and change tracking data can reveal information intended to remain confidential.
Regulatory compliance issues: If a public PDF exposes personal data, old draft labels, or internal comments, it can violate GDPR, CCPA, or other privacy regulations.
Proper metadata sanitization:
:path=/static-assets/pdf/content-code-examples/tutorials/encrypt-pdf-csharp/encrypt-pdf-csharp-pdf-security-metadata-sanitization--14.csusing IronPdf;
using System;
using System.Linq;
var pdf = PdfDocument.FromFile("input.pdf");
// Remove all standard metadata
pdf.MetaData.Author = "";
pdf.MetaData.Title = "";
pdf.MetaData.Subject = "";
pdf.MetaData.Keywords = "";
pdf.MetaData.Creator = "";
pdf.MetaData.Producer = "";
// Apply neutral metadata
pdf.MetaData.Title = "Document";
pdf.MetaData.Subject = "General Information";
pdf.MetaData.Producer = "PDF Generator";
pdf.SaveAs("output-sanitized.pdf");
Imports IronPdf
Imports System
Imports System.Linq
Dim pdf = PdfDocument.FromFile("input.pdf")
' Remove all standard metadata
pdf.MetaData.Author = ""
pdf.MetaData.Title = ""
pdf.MetaData.Subject = ""
pdf.MetaData.Keywords = ""
pdf.MetaData.Creator = ""
pdf.MetaData.Producer = ""
' Apply neutral metadata
pdf.MetaData.Title = "Document"
pdf.MetaData.Subject = "General Information"
pdf.MetaData.Producer = "PDF Generator"
pdf.SaveAs("output-sanitized.pdf")Sample Output (Removing Standard Metadata & Adding Neutral Metadata)
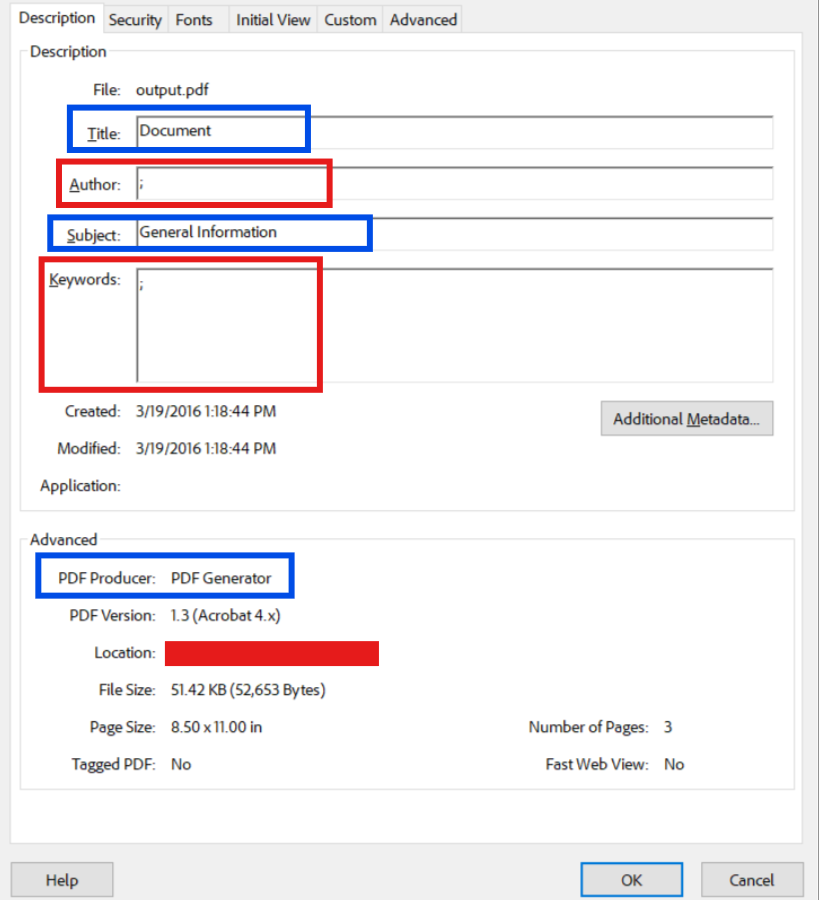
Complete PDF sanitization checklist:
- ✅ Remove author and creator information.
- ✅ Clear title, subject, and keyword fields.
- ✅ Strip creation and modification dates.
- ✅ Remove application and PDF producer information.
- ✅ Clear custom metadata properties.
- ✅ Remove embedded thumbnails.
- ✅ Strip document outline and bookmarks that reveal structure.
- ✅ Remove file attachments.
- ✅ Clear form field data and calculations.
- ✅ Remove JavaScript code.
- ✅ Strip digital signature information if replacing.
- ✅ Clear encryption dictionary if removing security.
For comprehensive metadata handling, consider these practices:
- Establish standardized metadata policies for external documents
- Implement automated metadata sanitization in document workflows
- Add metadata checks to your publishing and legal review workflows
- Train staff on metadata risks and proper handling
- Use consistent, neutral metadata for public documents
- Perform regular audits of published documents
For additional information on metadata and security settings, see our security and metadata guide.
Conclusion
From basic password protection to military-grade classified document handling, IronPDF offers the tools you need to implement robust security appropriate for your requirements. Whether you're protecting financial reports, legal contracts, healthcare records, or government documents, the security framework provided by IronPDF ensures your sensitive information remains confidential and tamper-proof.
Key takeaways for implementing PDF security with IronPDF:
- Use strong encryption with complex passwords for sensitive documents
- Implement the principle of least privilege with granular permission controls
- Combine multiple security layers (encryption, passwords, permissions, signatures)
- Properly sanitize documents before external distribution
- Avoid common anti-patterns that provide false security
- Maintain audit trails for classified and compliance-sensitive documents
- Regular review and update of security practices as threats evolve
By following the guidance in this tutorial and leveraging IronPDF's comprehensive security features, you can build document protection systems that meet the strictest enterprise and regulatory requirements. Remember that security is not a one-time implementation but an ongoing process of assessment, improvement, and vigilance.
If you have questions about IronPDF security features or want to request additional functionality, please reach out to our support team. We're committed to helping you implement the robust PDF security your applications demand.
Frequently Asked Questions
What are the benefits of using IronPDF for PDF encryption in C#?
IronPDF provides robust PDF encryption capabilities, allowing developers to secure documents with AES-128 encryption, set user and owner passwords, and control granular permissions to protect sensitive information effectively.
How can I encrypt a PDF using C# with IronPDF?
To encrypt a PDF using C# with IronPDF, you can use the library to specify encryption settings such as AES-128, set user and owner passwords, and define permissions for the document to restrict access and actions.
What types of permissions can be controlled in a PDF using IronPDF?
With IronPDF, you can control various permissions such as printing, copying, editing, and annotating the document, providing fine-grained security controls to meet specific security requirements.
Can IronPDF handle batch processing for PDF security?
Yes, IronPDF is capable of batch processing, allowing you to apply security settings to multiple PDF documents efficiently within .NET applications, saving time and ensuring consistent security across documents.
Is it possible to remove encryption from a PDF using IronPDF?
IronPDF allows you to modify or remove encryption from a PDF if you have the necessary permissions or passwords, providing flexibility in managing document security.
What encryption standards are supported by IronPDF?
IronPDF supports AES-128 encryption standard, which is a robust and widely-used method for securing PDF documents against unauthorized access.
How does IronPDF ensure the protection of sensitive documents in .NET applications?
IronPDF ensures the protection of sensitive documents by offering comprehensive encryption options, password protection, and detailed permission settings, allowing developers to implement secure document handling within .NET applications.



















